Prepared by:
HALBORN
Last Updated 04/25/2024
Date of Engagement by: March 21st, 2022 - March 28th, 2022
Summary
0% of all REPORTED Findings have been addressed
All findings
4
Critical
0
High
0
Medium
2
Low
2
Informational
0
Table of Contents
1. INTRODUCTION
BenQi engaged Halborn to conduct a security audit on their web apps beginning on March 21st, 2022 and ending on March 28th, 2022. The security assessment was scoped to the Web Application and its respective API. Halborn was provided access to the testing environment to conduct security testing using tools to scan, detect, validate possible vulnerabilities found in the application and report the findings at the end of the engagement.
Halborn recommends performing further testing to validate extended safety and correctness in context to the whole infrastructure when issues are fixed and new features added.
2. AUDIT SUMMARY
The team at Halborn was provided a timeline for the engagement and assigned one full-time security engineer to audit the security of the assets in scope. The engineer is a blockchain and smart contract security expert with advanced penetration testing, smart-contract hacking, and deep knowledge of multiple blockchain protocols.
The goals of our security audits are to improve the quality of systems by testing this as blackbox approach. We review and aim for sufficient remediation to help protect users.
In summary, Halborn identified some security risks that should be addressed by the BenQi team.
3. TEST APPROACH & METHODOLOGY
Halborn followed the Blackbox methodology and performed a combination of manual and automated security testing with both to balance efficiency, timeliness, practicality, and accuracy regarding the scope of the pentest. While manual testing is recommended to uncover flaws in logic, process and implementation; automated testing techniques assist enhance coverage of the infrastructure and can quickly identify flaws in it. The following phases and associated tools were used throughout the term of the audit:
Mapping Application Content and Functionality
Application Logic Flaws
Rate Limitations Tests
API misconfiguration
Input Handling
Google Cloud Bypass
Fuzzing of all input parameters
Test for Injection (SQL/JSON/HTML/Command)
4. SCOPE
The following URLs/APIs were in scope:
https://app.benqi.fi/https://staking.benqi.fi/https://api.benqi.fi/
5. RISK METHODOLOGY
- 5 - Almost certain an incident will occur.
- 4 - High probability of an incident occurring.
- 3 - Potential of a security incident in the long term.
- 2 - Low probability of an incident occurring.
- 1 - Very unlikely issue will cause an incident.
- 5 - May cause devastating and unrecoverable impact or loss.
- 4 - May cause a significant level of impact or loss.
- 3 - May cause a partial impact or loss to many.
- 2 - May cause temporary impact or loss.
- 1 - May cause minimal or un-noticeable impact.
- 10 - CRITICAL
- 9 - 8 - HIGH
- 7 - 6 - MEDIUM
- 5 - 4 - LOW
- 3 - 1 - VERY LOW AND INFORMATIONAL
6. SCOPE
7. Assessment Summary & Findings Overview
Critical
0
High
0
Medium
2
Low
2
Informational
0
Impact x Likelihood
HAL-02
HAL-01
HAL-04
HAL-03
| Security analysis | Risk level | Remediation Date |
|---|---|---|
| LACK OF RESOURCES AND RATE LIMITING | Medium | - |
| CLICKJACKING | Medium | - |
| INSECURE CORS CONFIGURATION | Low | - |
| OPTIONS HTTP METHOD ALLOWED | Low | - |
8. Findings & Tech Details
8.1 LACK OF RESOURCES AND RATE LIMITING
// Medium
Description
Requests to the BenQi API (https://api.benqi.fi/) consume resources such as network, CPU, memory, and storage. This vulnerability occurs when too many requests arrive simultaneously, and the API does not have enough compute resources to handle those requests. An attacker could exploit this vulnerability to overload the API by sending more requests than it can handle. As a result, the API becomes unavailable or unresponsive to new requests.
 {width="600" height="600"}
{width="600" height="600"}Score
Likelihood: 4
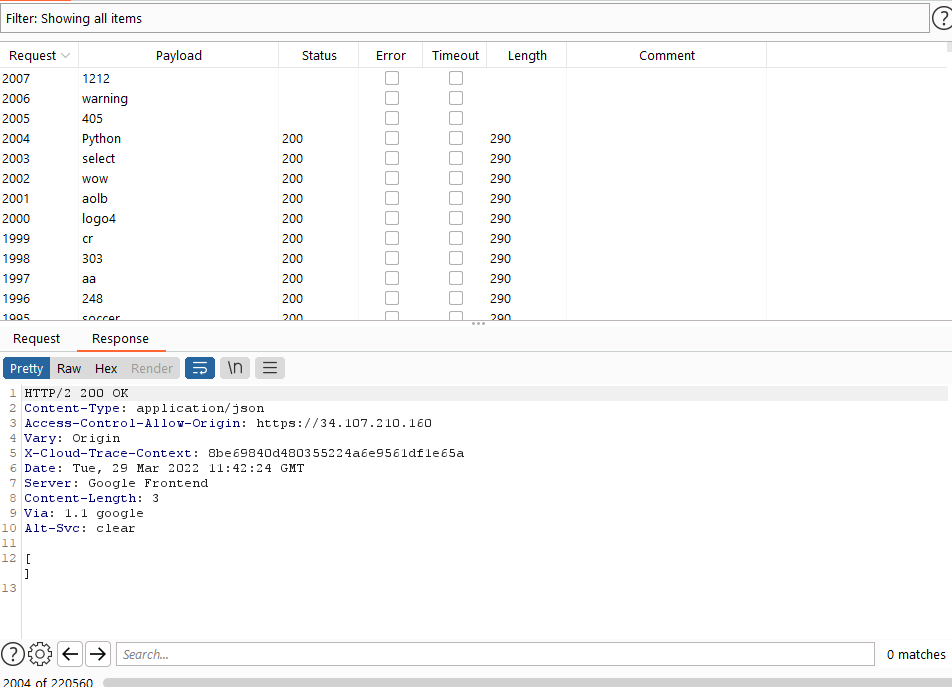
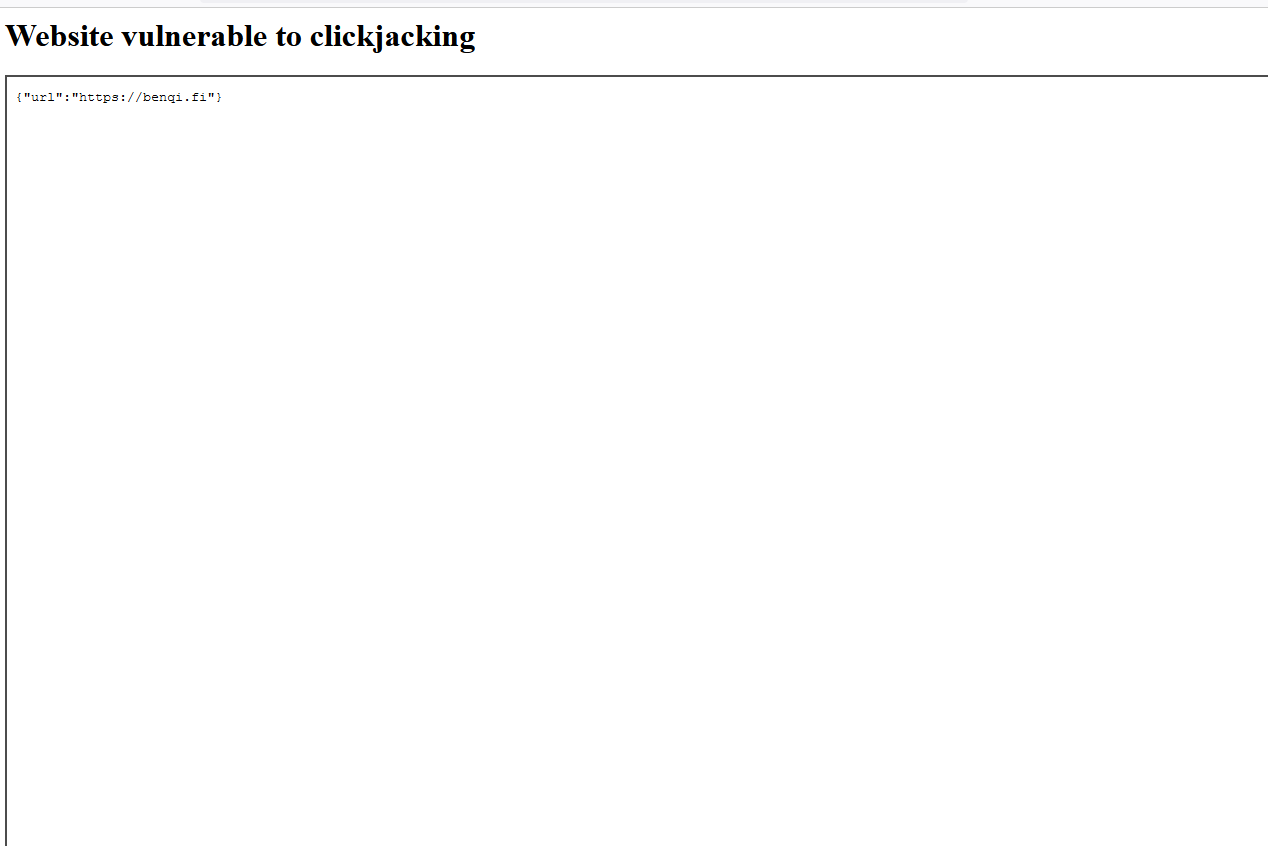
8.2 CLICKJACKING
// Medium
Description
The BenQi backend API https://api.benqi.fi, as well as the https://app.benqi.fi and https://staking.benqi.fi apps do not set a header. X-Frame-Options response header or a Content-Security-Policy 'frame-ancestors' response header on all content responses.
Clickjacking is a malicious technique to trick a Web user into clicking something other than what the user perceives, which could reveal sensitive information or take control of your computer while clicking on web pages that appear to be harmless.
 {width="600" height="600"}
{width="600" height="600"}https://api.benqi.fi/
GET / HTTP/1.1
Host: api.benqi.fi
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
Response
HTTP/1.1 200 OK
Content-Type: application/json
Access-Control-Allow-Origin: *
X-Cloud-Trace-Context: e0dc15074abf4a5d4f05e920a982202c
Date: Wed, 23 Mar 2022 11:50:54 GMT
Server: Google Frontend
Content-Length: 27
Via: 1.1 google
Alt-Svc: clear
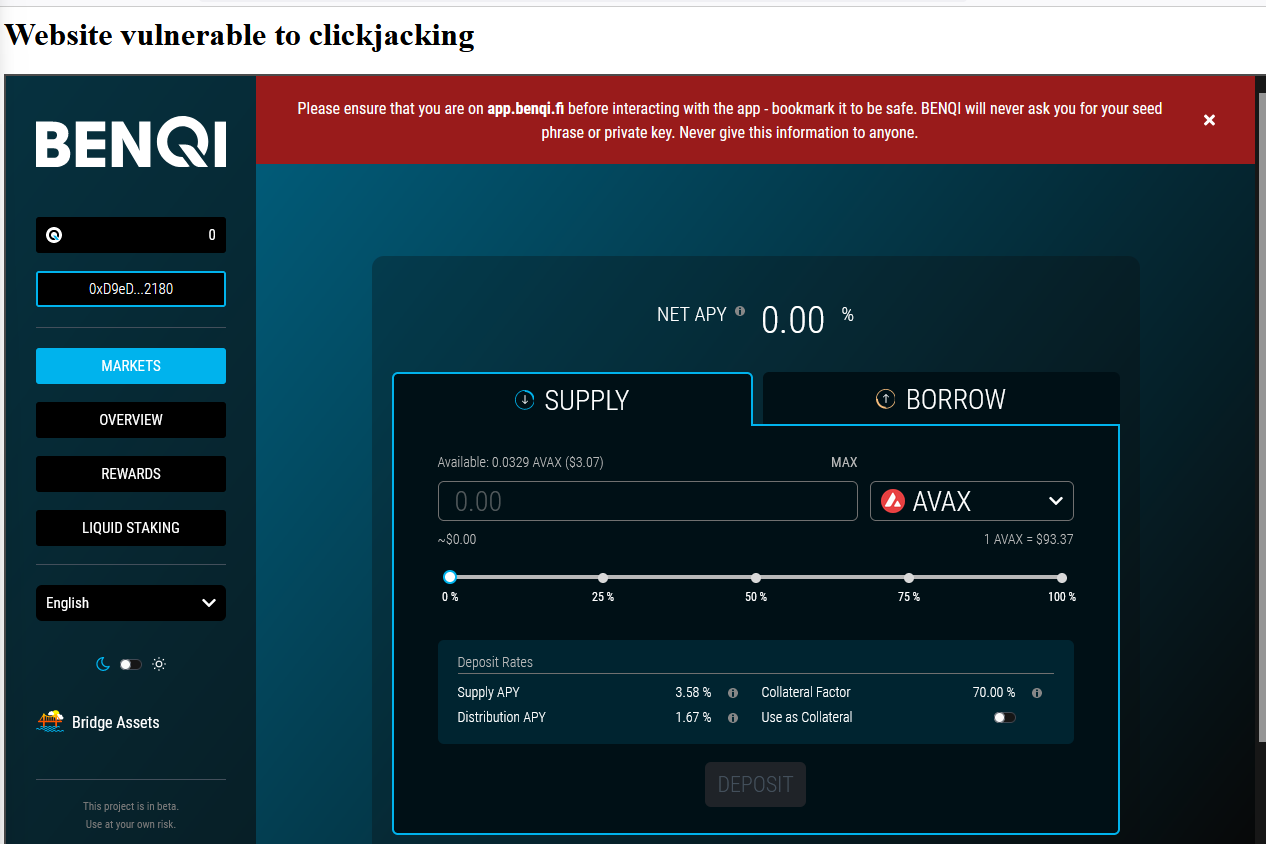 {width="600" height="600"}
{width="600" height="600"}https://app.benqi.fi/
GET / HTTP/1.1
Host: app.benqi.fi
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
Response
HTTP/1.1 200 OK
content-type: text/html
last-modified: Wed, 16 Feb 2022 15:51:25 GMT
etag: "620d1d7d-d11"
accept-ranges: bytes
X-Cloud-Trace-Context: c7538a33fe602f94750cf56050818f0a
Date: Tue, 22 Mar 2022 18:36:04 GMT
Server: Google Frontend
Content-Length: 3345
Via: 1.1 google
Alt-Svc: clear
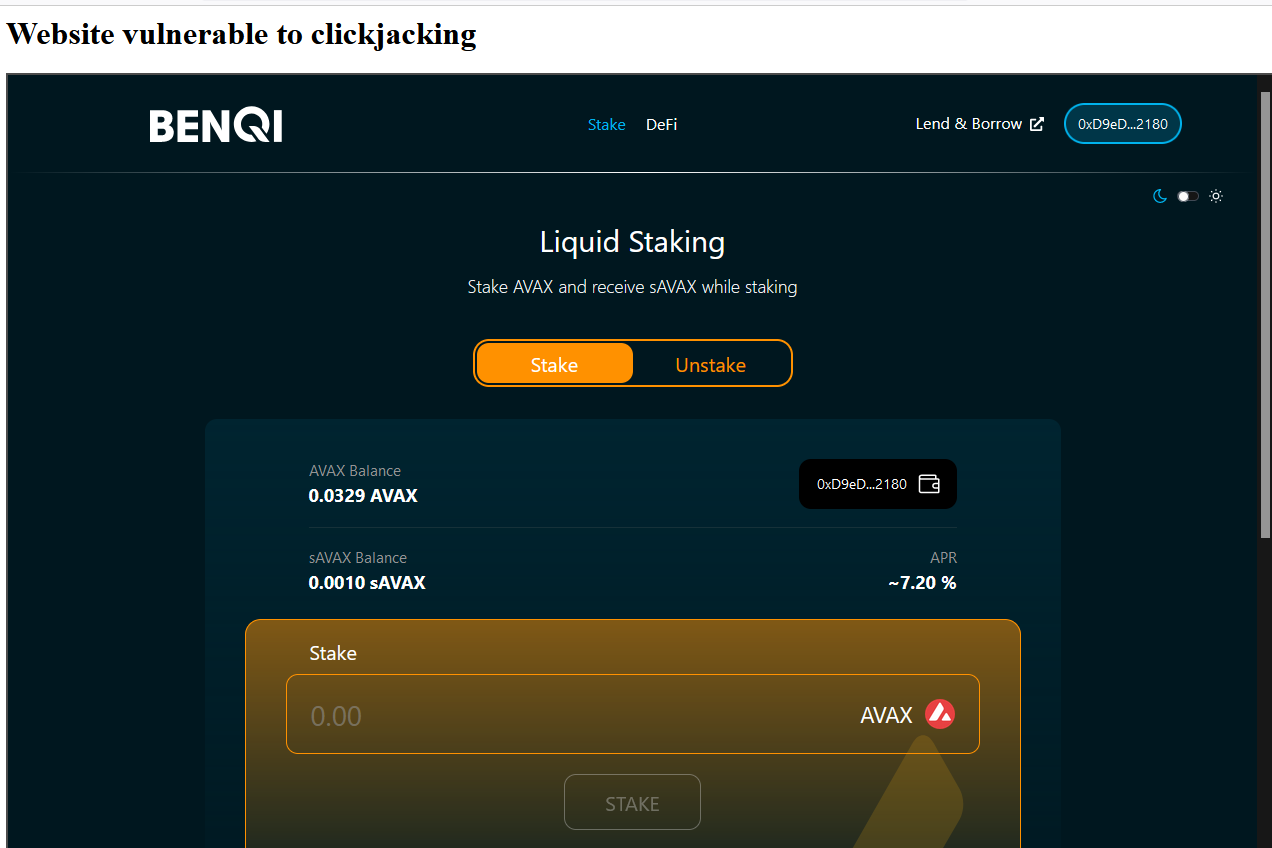 {width="600" height="600"}
{width="600" height="600"}https://staking.benqi.fi/
GET / HTTP/1.1
Host: staking.benqi.fi
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
Response
HTTP/1.1 200 OK
content-type: text/html
last-modified: Thu, 17 Mar 2022 11:33:27 GMT
etag: "62331c87-cf9"
accept-ranges: bytes
X-Cloud-Trace-Context: c48d1a87e621a00f80542e81488757ce
Date: Tue, 22 Mar 2022 18:37:58 GMT
Server: Google Frontend
Content-Length: 3321
Via: 1.1 google
Alt-Svc: clear
Score
Likelihood: 3
8.3 INSECURE CORS CONFIGURATION
// Low
Description
The BenQi backend API https://api.benqi.fi has an insecure CORS configuration, which allows any website to trigger requests with user credentials and read the responses.
This allows malicious users to perform potentially privileged actions or retrieve potential sensitive information.
https://api.benqi.fi/
GET / HTTP/1.1
Host: api.benqi.fi
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
HTTP/1.1 200 OK
Content-Type: application/json
Access-Control-Allow-Origin: *
X-Cloud-Trace-Context: e0dc15074abf4a5d4f05e920a982202c
Date: Wed, 23 Mar 2022 11:50:54 GMT
Server: Google Frontend
Content-Length: 27
Via: 1.1 google
Alt-Svc: clear
The Access-Control-Allow-Origin header is set to "*", which allows any website to trigger requests to https://api.benqi.fi/.
https://api.benqi.fi/users/0x...F/liquidations
GET /users/0xF9eD346aDf63ABb87f98231Eb0C29084e13D218F/liquidations HTTP/2
Host: api.benqi.fi
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://astrocamel.com
Origin: https://astrocamel.com
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: cross-site
Te: trailers
HTTP/2 200 OK
Content-Type: application/json
Access-Control-Allow-Origin: https://astrocamel.com
Vary: Origin
X-Cloud-Trace-Context: c571201d49ee7da2811e3b49b292c07b
Date: Tue, 29 Mar 2022 09:04:39 GMT
Server: Google Frontend
Content-Length: 3
Via: 1.1 google
Alt-Svc: clear
[]
The Access-Control-Allow-Origin header above is set to the "Origin" header request, further proving that any website can send requests to https://api.benqi.fi/.
Score
Likelihood: 3
8.4 OPTIONS HTTP METHOD ALLOWED
// Low
Description
The BenQi backend API server https://api.benqi.fi allows "OPTIONS" requests to be made against it.
This is not an immediate thread by itself, but the "OPTIONS" method can expose other methods that are supported by the web server, allowing attackers to gain additional information about the target system and restrict their attacks.
https://api.benqi.fi/
OPTIONS / HTTP/1.1
Host: api.benqi.fi
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
Allow: GET, HEAD, OPTIONS
Access-Control-Allow-Origin: *
X-Cloud-Trace-Context: ac46093c12645fccccf89998a31abf3b
Date: Wed, 23 Mar 2022 11:51:07 GMT
Server: Google Frontend
Content-Length: 0
Via: 1.1 google
Alt-Svc: clear
Currently allowed methods are not harmful, so the severity of this finding has been reduced.
Score
Likelihood: 2
9. Review Notes
SQL Injection Attack
Description
SQL injection is a code injection technique used to attack data-driven applications, in which malicious SQL statements are inserted into an input field for execution.
Goal
Determine the injection flaw and exploit it in application/API and make recommendations to defend against attacks.
Screenshots/Videos
SQL Injection Request
GET /users/0xF9eD346aDf63ABb87f98231Eb0C29084e13D218F/liquidations?limit=5&offset=0 HTTP/2
Host: api.benqi.fi
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://app.benqi.fi/
Origin: https://app.benqi.fi
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-site
Te: trailers
 {width="600" height="600"}
{width="600" height="600"}Result
No vulnerable SQLi parameters have been found.
Rate Limitation
Description
Rate limits define the maximum number of requests that can be sent in a given period of time. By implementing rate limiting, you protect your infrastructure from being overwhelmed by malicious requests and make your infrastructure available to legitimate users.
Goal
Determine security measures against the number of requests in a short time frame.
Result
The vulnerable endpoint is reported above.
Fuzzing
Description
Fuzz testing or Fuzzing is a Black Box software testing technique, which consists of a wide range of invalid and unexpected data into an application, then monitoring the application for exceptions and crashes.
Goal
Fuzz parameters and determine any unexpected crashes against provided input handling to find vulnerabilities.
Screenshots/Videos
 {width="600" height="600"}
{width="600" height="600"} {width="600" height="600"}
{width="600" height="600"}Result
No exceptions/vulnerabilities found.
Web Cache Poisoning
Description
Web cache poisoning is a technique whereby an attacker exploits the behavior of a web server and cache so that a harmful HTTP response is served to other users.
Goal
To pinpoint a malicious response by the server and force it to be stored on the server cache, so that all users who request a specific resource are served with that malicious resource.
Result
No unencrypted vulnerable inputs detected.
Directory Bruteforce
Description
DirBuster is a technique designed to brute force directories and files names on web/application servers. DirBuster searches for hidden pages and directories on a web server. Sometimes developers will leave a page accessible, but not linked. DirBuster is intended to find these potential vulnerabilities.
Goal
To determine hidden/vulnerable pages and directories on a web server that are not required (or should not even be public) and this could help a malicious user to perform further attacks.
Result
No vulnerable/sensitive directory detected.
Halborn strongly recommends conducting a follow-up assessment of the project either within six months or immediately following any material changes to the codebase, whichever comes first. This approach is crucial for maintaining the project’s integrity and addressing potential vulnerabilities introduced by code modifications.
Table of Contents
// Download the full report
* Use Google Chrome for best results
** Check "Background Graphics" in the print settings if needed
