Prepared by:
HALBORN
Last Updated 02/17/2025
Date of Engagement: January 28th, 2025 - February 5th, 2025
Summary
100% of all REPORTED Findings have been addressed
All findings
34
Critical
0
High
0
Medium
0
Low
12
Informational
22
Table of Contents
- 1. Introduction
- 2. Assessment summary
- 3. Test approach and methodology
- 4. Risk methodology
- 5. Scope
- 6. Assessment summary & findings overview
- 7. Findings & Tech Details
- 7.1 Incorrect order of modifiers: nonreentrant should be the first
- 7.2 Non-payable owner would dos corevault
- 7.3 Initializers could be front-run
- 7.4 Implementation contracts can be initialized
- 7.5 Inconsistent timestamp comparisons exclude exact unlock time
- 7.6 Ineffective remaining dualcore balance check
- 7.7 Lack of storage gap in upgradeable contract
- 7.8 Division by zero not prevented
- 7.9 Missing input validation
- 7.10 Missing array length validation in reinvest
- 7.11 Potential rounding errors
- 7.12 Centralization risk
- 7.13 Direct inclusion and modification of openzeppelin modules leading to inconsistencies
- 7.14 Corevault in dualcore address could be immutable
- 7.15 Contract name reused in different files
- 7.16 Owner can renounce ownership
- 7.17 Enumerableset.remove() in loop corrupts the set order
- 7.18 Incorrect bounds checking in getreceivers() reverts with empty receivers
- 7.19 Incomplete natspec documentation
- 7.20 Potential license incompatibilities
- 7.21 Lack of event emission
- 7.22 Debugging import included in production code
- 7.23 Magic numbers in use
- 7.24 Unlocked pragma compiler
- 7.25 Use of revert strings instead of custom error
- 7.26 Consider using named mappings
- 7.27 Style guide optimizations
- 7.28 Cache array length outside of loop
- 7.29 Events missing indexed fields
- 7.30 Mixed msg.sender and _msgsender
- 7.31 Inconsistency declaring uint256/uint
- 7.32 Unused or dead code
- 7.33 Legacy/confusing naming
- 7.34 Ignored return values
- 8. Automated Testing
1. Introduction
CoreDAO engaged Halborn to conduct a security assessment of the new B14G Contracts project by B14G beginning on January 28th and ending on February 05th. The security assessment was scoped to the smart contracts in the contracts GitHub repository of b14glabs provided to the Halborn team. Commit hashes and further details can be found in the Scope section of this report.
2. Assessment Summary
Halborn was provided 3.5 days for the engagement and assigned one full-time security engineer to review the security of the smart contract in scope. The engineer is a blockchain and smart contract security expert with advanced penetration testing and smart contract hacking skills, and deep knowledge of multiple blockchain protocols.
The purpose of the assessment is to:
Identify potential security issues within the smart contracts.
Ensure that smart contract functionality operates as intended.
In summary, Halborn identified some improvements to reduce the likelihood and impact of risks, which were partially addressed by the B14G team. The main ones are the following:
Ensure the nonReentrant modifier is always the first modifier in all functions.Make sure the owner address of CoreVault can accept native funds to avoid denial of service issues.Ensure initializers cannot be frontrun by including the initialization in the proxy creation or by using a factory.
3. Test Approach and Methodology
Halborn performed a combination of manual and automated security testing to balance efficiency, timeliness, practicality, and accuracy in regard to the scope of this assessment. While manual testing is recommended to uncover flaws in logic, process, and implementation; automated testing techniques help enhance coverage of the code and can quickly identify items that do not follow the security best practices. The following phases and associated tools were used during the assessment:
Research into architecture and purpose.
Smart contract manual code review and walkthrough.
Graphing out functionality and contract logic/connectivity/functions (
solgraph).Manual assessment of use and safety for the critical Solidity variables and functions in scope to identify any arithmetic related vulnerability classes.
Manual testing by custom scripts.
Static Analysis of security for scoped contract, and imported functions (
slither).Testnet deployment (
HardhatandFoundry).
4. RISK METHODOLOGY
4.1 EXPLOITABILITY
Attack Origin (AO):
Attack Cost (AC):
Attack Complexity (AX):
Metrics:
| EXPLOITABILITY METRIC () | METRIC VALUE | NUMERICAL VALUE |
|---|---|---|
| Attack Origin (AO) | Arbitrary (AO:A) Specific (AO:S) | 1 0.2 |
| Attack Cost (AC) | Low (AC:L) Medium (AC:M) High (AC:H) | 1 0.67 0.33 |
| Attack Complexity (AX) | Low (AX:L) Medium (AX:M) High (AX:H) | 1 0.67 0.33 |
4.2 IMPACT
Confidentiality (C):
Integrity (I):
Availability (A):
Deposit (D):
Yield (Y):
Metrics:
| IMPACT METRIC () | METRIC VALUE | NUMERICAL VALUE |
|---|---|---|
| Confidentiality (C) | None (I:N) Low (I:L) Medium (I:M) High (I:H) Critical (I:C) | 0 0.25 0.5 0.75 1 |
| Integrity (I) | None (I:N) Low (I:L) Medium (I:M) High (I:H) Critical (I:C) | 0 0.25 0.5 0.75 1 |
| Availability (A) | None (A:N) Low (A:L) Medium (A:M) High (A:H) Critical (A:C) | 0 0.25 0.5 0.75 1 |
| Deposit (D) | None (D:N) Low (D:L) Medium (D:M) High (D:H) Critical (D:C) | 0 0.25 0.5 0.75 1 |
| Yield (Y) | None (Y:N) Low (Y:L) Medium (Y:M) High (Y:H) Critical (Y:C) | 0 0.25 0.5 0.75 1 |
4.3 SEVERITY COEFFICIENT
Reversibility (R):
Scope (S):
Metrics:
| SEVERITY COEFFICIENT () | COEFFICIENT VALUE | NUMERICAL VALUE |
|---|---|---|
| Reversibility () | None (R:N) Partial (R:P) Full (R:F) | 1 0.5 0.25 |
| Scope () | Changed (S:C) Unchanged (S:U) | 1.25 1 |
| Severity | Score Value Range |
|---|---|
| Critical | 9 - 10 |
| High | 7 - 8.9 |
| Medium | 4.5 - 6.9 |
| Low | 2 - 4.4 |
| Informational | 0 - 1.9 |
5. SCOPE
- contracts/marketplace/MergeMarketplaceStrategy.sol
- contracts/marketplace/CoreVault.sol
- contracts/erc20/IERC20.sol
6. Assessment Summary & Findings Overview
Critical
0
High
0
Medium
0
Low
12
Informational
22
| Security analysis | Risk level | Remediation Date |
|---|---|---|
| Incorrect Order of Modifiers: nonReentrant Should Be the First | Low | Risk Accepted - 02/13/2025 |
| Non-Payable Owner Would DoS CoreVault | Low | Risk Accepted - 02/13/2025 |
| Initializers Could Be Front-run | Low | Risk Accepted - 02/13/2025 |
| Implementation Contracts Can Be Initialized | Low | Future Release - 02/13/2025 |
| Inconsistent Timestamp Comparisons Exclude Exact Unlock Time | Low | Solved - 02/11/2025 |
| Ineffective Remaining dualCore Balance Check | Low | Future Release - 02/13/2025 |
| Lack Of Storage Gap In Upgradeable Contract | Low | Risk Accepted - 02/13/2025 |
| Division by Zero Not Prevented | Low | Not Applicable - 02/13/2025 |
| Missing Input Validation | Low | Future Release - 02/13/2025 |
| Missing Array Length Validation in reInvest | Low | Solved - 02/11/2025 |
| Potential Rounding Errors | Low | Risk Accepted - 02/13/2025 |
| Centralization Risk | Low | Future Release - 02/13/2025 |
| Direct Inclusion and Modification of OpenZeppelin Modules Leading to Inconsistencies | Informational | Future Release - 02/13/2025 |
| CoreVault in DualCore Address Could Be Immutable | Informational | Acknowledged - 02/13/2025 |
| Contract Name Reused in Different Files | Informational | Future Release - 02/13/2025 |
| Owner Can Renounce Ownership | Informational | Acknowledged - 02/13/2025 |
| EnumerableSet.remove() in Loop Corrupts The Set Order | Informational | Acknowledged - 02/13/2025 |
| Incorrect bounds checking in getReceivers() reverts with empty receivers | Informational | Future Release - 02/13/2025 |
| Incomplete NatSpec Documentation | Informational | Acknowledged - 02/13/2025 |
| Potential License Incompatibilities | Informational | Future Release - 02/13/2025 |
| Lack of Event Emission | Informational | Future Release - 02/13/2025 |
| Debugging Import Included in Production Code | Informational | Future Release - 02/13/2025 |
| Magic Numbers in Use | Informational | Future Release - 02/13/2025 |
| Unlocked Pragma Compiler | Informational | Future Release - 02/13/2025 |
| Use of Revert Strings Instead of Custom Error | Informational | Future Release - 02/13/2025 |
| Consider Using Named Mappings | Informational | Acknowledged - 02/13/2025 |
| Style Guide Optimizations | Informational | Acknowledged - 02/13/2025 |
| Cache Array Length Outside of Loop | Informational | Future Release - 02/13/2025 |
| Events Missing Indexed Fields | Informational | Future Release - 02/13/2025 |
| Mixed msg.sender and _msgSender | Informational | Future Release - 02/13/2025 |
| Inconsistency Declaring uint256/uint | Informational | Acknowledged - 02/13/2025 |
| Unused or Dead Code | Informational | Future Release - 02/13/2025 |
| Legacy/Confusing Naming | Informational | Future Release - 02/13/2025 |
| Ignored Return Values | Informational | Acknowledged - 02/13/2025 |
7. Findings & Tech Details
7.1 Incorrect Order of Modifiers: nonReentrant Should Be the First
//
Description
The nonReentrant modifier is a critical security measure used in Solidity to prevent reentrancy attacks. It acts as a function-level lock, ensuring that a function cannot be called again before it finishes its execution. To maximize its effectiveness, the nonReentrant modifier must be placed as the first modifier in a function declaration. This ordering ensures that reentrancy protection is applied before any other logic or checks in other modifiers are executed.
Currently, some functions in the project place other modifiers, such as whenNotPaused and onlyDualCore, before the nonReentrant modifier. This improper ordering can lead to scenarios where external calls in preceding modifiers might be exploited to bypass the reentrancy protection provided by nonReentrant.
Instances:
In
CoreVault, thestake(),withdrawDirect(),unbond(),withdraw()functions have thewhenNotPausedmodifier before thenonReentrant.In
MergeMarketplaceStrategy, thewithdraw()hasonlyDualCoremodifier before thenonReentrant.
BVSS
Recommendation
Reorder the nonReentrant modifier to precede all other modifiers in the affected functions. This ensures that reentrancy protection is enforced before any additional checks or logic are applied.
Remediation
RISK ACCEPTED: The B14G team accepted the risk of this finding.
7.2 Non-Payable Owner Would DoS CoreVault
//
Description
Several functions in the CoreVault contract, namely withdrawDirect() and claimReward(), implement fee transfers by directly pushing native tokens to the owner via calls such as:
Address.sendValue(payable(owner()), fee);This mechanism assumes that the owner is a payable address. However, if the owner is updated to a non-payable address (for instance, a contract lacking a payable fallback or receive function), the fee transfer will fail. Since these fee transfers are integral to the respective functions’ execution, the failure will cause the entire transaction to revert. As a result, users may be unable to withdraw funds or claim rewards, effectively locking funds and creating a denial-of-service situation.
BVSS
Recommendation
Consider adopting a pull-over-push pattern for fee distribution. Instead of automatically transferring fees to the owner during each transaction, accumulate the fees within the contract (or another collector contract) and provide a dedicated withdrawal function that allows the owner to pull the accumulated fees. This approach decouples fee distribution from critical user operations, thereby preventing transaction reversion due to non-payable recipient issues.
Remediation
RISK ACCEPTED: The B14G team accepted the risk of this finding.
7.3 Initializers Could Be Front-run
//
Description
According to the documentation, CoreVault, Marketplace and MergeMarketplaceStrategy contracts are meant to be upgradeable contracts. Initializers could be front-run, allowing an attacker to either set their own values, take ownership of the contract, and in the best case forcing a re-deployment.
Analyzing the deployment scripts, it can be observed that implementations are first deployed, then the proxies (using ProxyAdmin) and, finally, the proxies are initialized:
const CoreVault = await ethers.getContractFactory("CoreVault");
const coreVaultImpl = await CoreVault.deploy();
await coreVaultImpl.deployed();
const coreVaultProxy = await ProxyAdmin.deploy(coreVaultImpl.address, accounts[0].address);
await coreVaultProxy.deployed();
console.log("CoreVault deployed to:", coreVaultProxy.address);
const coreVault = CoreVault.attach(coreVaultProxy.address);
let tx = await coreVault.initialize(accounts[0].address, accounts[0].address, 1000, 100, 1800, parseEther("100000"));
await tx.wait();And testing too:
const CoreVault = await ethers.getContractFactory("CoreVault");
const coreVaultImpl = await CoreVault.deploy();
const coreVaultProxy = await ProxyAdmin.deploy(coreVaultImpl.address, accounts[0].address);
const coreVault = CoreVault.attach(coreVaultProxy.address);
await coreVault.initialize(accounts[0].address, accounts[0].address, 1000, 100, 86400, parseEther("100"));BVSS
Recommendation
It is recommended the following:
Include initialization call in the proxy setup
Use a factory to deploy and intializer in the same transaction.
Remediation
RISK ACCEPTED: The B14G team accepted the risk of this finding.
7.4 Implementation Contracts Can Be Initialized
//
Description
According to the documentation, CoreVault, MergeMarketplaceStrategy and Marketplace contracts are upgradeable contracts. In order to prevent leaving the contracts uninitialized, OpenZeppelin's documentation recommends adding the _disableInitializers() function in the constructor to automatically lock the contracts when they are deployed. However, all upgradeable contracts in scope are missing this protection.
This omission can lead to potential security vulnerabilities, as an uninitialized implementation contract can be taken over by an attacker, which may impact the proxy.
BVSS
Recommendation
Consider adding a constructor and calling the _disableinitializers() method from the OpenZeppelin module Initializable to prevent the implementation from being initialized.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.5 Inconsistent Timestamp Comparisons Exclude Exact Unlock Time
//
Description
The CoreVault contract uses strict less than (<) comparisons when checking if unbond records are ready for withdrawal or unlocked. This means users cannot withdraw or see their funds as unlocked exactly at the unlock time, which is inconsistent with common DeFi practices and standards like EIP-2612.
In the
withdraw()function:
if (record.unlockTime < block.timestamp) {
...
}In the
getUnbondAmount():
if (records[i].unlockTime < block.timestamp) {
unlockedAmount += records[i].coreAmount;
} else {
lockedAmount += records[i].coreAmount;
}BVSS
Recommendation
Consider changing all timestamp comparisons to be inclusive by using <= or >= as appropriate.
Remediation
SOLVED: The B14G team fixed this finding in commit d91991a by adjusting the timestamp comparison as recommended.
Remediation Hash
7.6 Ineffective Remaining dualCore Balance Check
//
Description
In the CoreVault contract, the withdrawDirect() function attempts to ensure that a user’s remaining dualCore balance either meets a minimum threshold of 1 ether (in CORE equivalent) or is zero. However, this validation can be bypassed under certain conditions, making the check ineffective in preventing improper withdrawals:
function withdrawDirect(uint256 dualCoreAmount, bool claim) external payable whenNotPaused nonReentrant {
if (claim) claimReward();
uint256 coreAmount = exchangeCore(dualCoreAmount);
require(coreAmount >= 1 ether, "Amount too low");
IDualCore(dualCore).burn(msg.sender, dualCoreAmount);
uint256 remainDualCore = IDualCore(dualCore).balanceOf(msg.sender);
require(remainDualCore == 0 || exchangeCore(remainDualCore) >= 1 ether, "Remain amount too low");
...In this function, a user can bypass the remainDualCore balance validation by transferring a small amount of dualCore tokens to another account before calling withdrawDirect(). This circumvents the intent of the check and may allow withdrawals that do not fully meet the specified threshold.
Proof of Concept
The following test function shows how it is not possible to call withdrawDirect() if the remaining is going to be too low. However, a user can just transfer out some tokens to successfully bypass the check.
it("withdrawDirect", async () => {
// Get required contracts and accounts from fixture
const { coreVault, accounts, orderStrategy, coreAgent, candidate, dualCore } = await loadFixture(deployContracts);
// Get initial total staked and supply amounts
let totalStaked = await coreVault.callStatic.totalStaked();
let totalSupply = await dualCore.totalSupply();
// Verify exchange rate calculation
expect(await coreVault.callStatic.exchangeDualCore(BigNumber.from("10"))).to.eq(BigNumber.from("10").mul(totalSupply).div(totalStaked));
// Update totals
totalStaked = await coreVault.callStatic.totalStaked();
totalSupply = await dualCore.totalSupply();
// Test validation checks
await expect(coreVault.withdrawDirect(parseEther("0.5"), false)).to.revertedWith("Amount too low");
await expect(coreVault.withdrawDirect(parseEther("19.5"), false)).to.revertedWith("Remain amount too low");
// Bypass validation check
await dualCore.transfer(accounts[1].address, parseEther("0.5"));
//Successfully withdraw
await expect(coreVault.withdrawDirect(parseEther("19.5"), false)).not.to.be.reverted;
});BVSS
Recommendation
Consider redesigning the validation logic for the remaining dualCore balance to either improve or remove the verification.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.7 Lack Of Storage Gap In Upgradeable Contract
//
Description
The MergeMarketplaceStrategy contract is supposed to be designed to be an upgradeable contract. It inherits from OnwnableWithPausable, but it lacks storage gaps. Storage gaps are essential for ensuring that new state variables can be added in future upgrades without affecting the storage layout of inheriting child contracts. Without it, any addition of new state variables in future contract versions can lead to storage collisions.
BVSS
Recommendation
Consider adding a storage gap as the last storage variable to the implementation contracts, specially those meant to be inherited like OnwnableWithPausable.
Remediation
RISK ACCEPTED: The B14G team accepted the risk of this finding.
7.8 Division by Zero Not Prevented
//
Description
In CoreVault, the _exchangeDualCore() function performs a division without validating that denominators is non-zero. This unchecked divisions could lead to unexpected reverts and denial of service in edge cases.
function _exchangeDualCore(uint256 core) private returns (uint256) {
uint256 totalSupply = IDualCore(dualCore).totalSupply();
if (totalSupply == 0) {
return core;
}
uint256 totalCore = totalStaked() - core;
return core.mulDiv(totalSupply, totalCore);
}The vulnerability can occur when totalStaked() equals core and it makes totalCore = 0. The mulDiv() operation will then attempt to divide by zero, causing the transaction to revert.
BVSS
Recommendation
Consider adding a check for zero division:
function _exchangeDualCore(uint256 core) private returns (uint256) {
uint256 totalSupply = IDualCore(dualCore).totalSupply();
if (totalSupply == 0) {
return core;
}
uint256 totalCore = totalStaked() - core;
require(totalCore > 0, "CoreVault: division by zero"); // Added check
return core.mulDiv(totalSupply, totalCore);
}Remediation
NOT APPLICABLE: After a discussion with the B14G team, it was determined that this was a false positive, so it is not applicable.
7.9 Missing Input Validation
//
Description
During the security assessment, it was identified that some functions across the smart contracts lack proper input validation, allowing critical parameters to be set to undesired or unrealistic values. This can lead to potential vulnerabilities, unexpected behavior, or erroneous states within the contract.
Examples include, but are not limited to:
All
initialize()functions of the project are missing input validation.Most of the setters also lack a proper input validation. Therefore, for instance, it is possible to set an unlock period of 0 or unrealistically large.
updateDualCore()andupdateMarketplace()inMergeMarketplaceStrategy.
This list is not exhaustive. It is recommended to conduct a comprehensive review of the codebase to identify and assess other functions that may require additional input validation. Ensuring appropriate checks are in place for critical parameters will enhance the overall reliability, security, and predictability of the contracts.
BVSS
Recommendation
To mitigate these issues, implement input validation in all constructor functions and other critical functions to ensure that inputs meet expected criteria. This can prevent unexpected behaviors and potential vulnerabilities.
One example would be: Given that stake() does not allow the total supply of dualCORE to be greater than maxCap, if the owner ever updates maxCap, it could be reasonable to not be able to make it lower than the total supply of dualCORE:
function setMaxCap(uint256 _maxCap) external onlyOwner {
require(_maxCap >= IDualCore(dualCore).totalSupply(), "New max cap must be >= current total supply");
maxCap = _maxCap;
emit SetMaxCap(_maxCap);
}Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.10 Missing Array Length Validation in reInvest
//
Description
In the MergeMarketplaceStrategy contract, the reInvest() function accepts three arrays (withdrawData, stakeData, and indexReceivers) through encoded input data but does not validate their lengths relative to each other. The function uses indexReceivers to validate both withdrawal and stake operations. Specifically, indexReceivers[i] is used for withdrawals, and indexReceivers[i + withdrawData.length] is used for stakes.
Code snippet:
function reInvest(bytes calldata data) external payable nonReentrant onlyDualCore {
(bytes memory changeData, uint totalAmount) = abi.decode(data, (bytes, uint));
{
IMarketplace.WithdrawParam[] memory withdrawData;
IMarketplace.StakeParam[] memory stakeData;
uint[] memory indexReceivers;
(withdrawData, stakeData, indexReceivers) = abi.decode(changeData, (IMarketplace.WithdrawParam[], IMarketplace.StakeParam[], uint[]));
if (withdrawData.length > 0) {
for (uint i = 0; i < withdrawData.length; i++) {
require(
IMarketplace(marketplace).getRewardReceiverBatch(indexReceivers[i], indexReceivers[i] + 1)[0] == withdrawData[i].receiver,
"invalid receiver"
);
}
IMarketplace(marketplace).withdrawCoreProxy(withdrawData);
}
if (stakeData.length > 0) {
uint stakeValue;
for (uint i = 0; i < stakeData.length; i++) {
require(
IMarketplace(marketplace).getRewardReceiverBatch(indexReceivers[i + withdrawData.length], indexReceivers[i + withdrawData.length] + 1)[Without explicit length validation, this can lead to several issues:
Array Out-of-Bounds Access: If
indexReceivers.lengthis less thanwithdrawData.length + stakeData.length, the function may access invalid array indices, potentially causing a transaction revert.Invalid Receiver Validation: Incorrect or incomplete input data may cause the
requirestatements to fail during validation checks.
BVSS
Recommendation
Add explicit length validation after decoding changeData to ensure that the lengths of the arrays are consistent. For example:
require(
indexReceivers.length == withdrawData.length + stakeData.length,
"Invalid input array lengths"
);Remediation
SOLVED: The B14G team fixed this finding in commit 09483cc by implementing the recommended array length validation.
Remediation Hash
7.11 Potential Rounding Errors
//
Description
The CoreVault contract calculates fees and adjusts rewards using integer division, which inherently truncates any fractional values. This approach may introduce rounding errors in fee and reward computations:
In
claimReward():
function claimReward() public whenNotPaused returns (uint256 reward) {
reward = IStrategy(strategy).claimReward();
if (reward > 0) {
uint fee = (reward * rewardFee) / 10000;
reward = reward - fee;
emit ClaimReward(reward, fee);
Address.sendValue(payable(owner()), fee);
}
}Here, the fee is computed as (reward * rewardFee) / 10000. For small reward values, the truncation due to integer division can lead to:
Minor discrepancies in the net reward allocated to the user.
Situations where the fee might be rounded down to zero, thus not reflecting the intended deduction.
BVSS
Recommendation
To mitigate precision loss and ensure fair fee and reward calculations, it is advisable to:
Implement Scaling Techniques:
Apply a scaling factor to the numerator before performing the division, preserving the fractional component.
Adjust the result accordingly after the division by reversing the scaling factor.
Consistent Calculation Updates:
Ensure that all fee and reward calculations in the contract are updated to use the scaling technique, thereby maintaining consistency.
Comprehensive Testing:
Thoroughly test the modified calculations with a range of edge cases, including very small and large values, to verify that the scaling approach reliably maintains accuracy without introducing unintended behavior.
Implementing these changes will enhance the precision of fee deductions and reward distributions, ensuring that users receive fair and predictable outcomes regardless of the transaction size.
Remediation
RISK ACCEPTED: The B14G team accepted the risk of this finding because "the rounding differences are extremely small, so any discrepancies in fee and reward computations are negligible and well within acceptable limits".
7.12 Centralization Risk
//
Description
The contracts implement extensive owner privileges through Ownable2Step inheritance, granting significant control over critical protocol parameters and functionality. Furthermore, in the RewardReceiver contract, the owner address cannot be changed.
This centralization of power creates significant risks:
Protocol functionality could be compromised if owner keys are lost or stolen.
Users funds could be affected through malicious fee manipulation.
Single point of failure in critical protocol operations.
BVSS
Recommendation
Consider the following recommendations:
Implement Multi-Signature Requirements: Require multi-signature approval for critical functions. This distributes control and mitigates the risk of unilateral actions by a single party.
Introduce Governance Mechanisms: Consider integrating on-chain governance to manage changes to depositories and transfer permissions. This would enable the community to have a say in significant decisions and enhance decentralization.
Add Role-Based Restrictions: Limit the
ownerrole's power by creating additional roles or access levels for specific functions.Time Locks: Introduce time locks for critical functions, such as modifying depositories, changing transfer permissions, or altering the minter role. This allows stakeholders to review proposed changes and act if necessary before the changes are finalized. Time locks enhance transparency and provide a safeguard against unilateral and immediate decisions.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.13 Direct Inclusion and Modification of OpenZeppelin Modules Leading to Inconsistencies
//
Description
The review identified that the project directly includes copies of OpenZeppelin modules within its repository (e.g., some files under contracts/erc20/, contracts/utils/ and contracts/library/) and applies modifications to these files. Notably, the project contains:
Two separate copies of the
Address.solfile (one undercontracts/library/and another undercontracts/utils/), each marked with "OpenZeppelin Contracts (last updated v4.8.0) (utils/Address.sol)".A custom interface
IDualCore.solthat is derived from the OpenZeppelinIERC20.solinterface with modifications.
Additionally, contracts like CoreVault and MergeMarketplaceStrategy use a custom OnwnableWithPausable module, which is a combination of Ownable2Step and Pausable. However, Marketplace is also using Ownable2Step, but implementing the pausable logic inside. Furthermore, notice the OnwnableWithPausable module has a typo and should be OwnableWithPausable instead.
Finally, a further issue was observed with the Math library. In version v4.8.0 of the included OpenZeppelin contracts, the function log256 is documented incorrectly. The outdated documentation comment reads:
/**
* @dev Return the log in base 10, following the selected rounding direction, of a positive value.
* Returns 0 if given 0.
*/Whereas the correct documentation (as updated in later commits, see commit 3a3c87b1a676f277c17a4601de56ddfc432d427d) should specify that the function returns the log in base 256. Retaining an outdated and incorrect version not only causes confusion for auditors and developers but also raises the risk of misinterpretation or misimplementation of mathematical operations.
This approach poses several risks:
Security and Maintenance Drift: OpenZeppelin contracts are thoroughly audited and maintained. By copying and modifying these files, the project bypasses the continuous improvements and security patches provided by the official library. This may inadvertently introduce vulnerabilities or inconsistencies with the audited versions.
Upgrade and Compatibility Issues: Custom modifications mean that future updates or bug fixes released by OpenZeppelin will not be automatically integrated. This increases the risk of the project using outdated or insecure implementations.
Code Duplication and Divergence: Maintaining multiple copies of similar code (as seen with
Address.sol) can lead to inconsistencies and maintenance challenges. This duplication increases the attack surface and complicates the auditing and review process.
BVSS
Recommendation
It is recommended the following:
Utilize Dependency Management: Instead of copying OpenZeppelin contracts directly into the repository, consider using a package manager (such as npm or yarn) to include the OpenZeppelin libraries as external dependencies. This practice ensures access to the latest security updates and improvements.
Minimize Unnecessary Modifications: When modifications are necessary, it is recommended to fork the OpenZeppelin repository and document the changes along with their justifications.
Eliminate Redundant Code: Remove duplicate copies of modules (for instance, consolidate the
Address.solfile into a single location) to prevent inconsistencies and simplify future updates.
By adhering to these recommendations, the project can benefit from the robust security and maintenance practices provided by the official OpenZeppelin libraries while minimizing the risks associated with direct modifications and code duplication.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.14 CoreVault in DualCore Address Could Be Immutable
//
Description
The DualCore contract allows setting the coreVault address post-deployment via setCoreVaultAddress(), even though this can only be called once. This pattern is less efficient than making the address immutable and setting it in the constructor:
function setCoreVaultAddress(address _coreVault) external onlyOwner calledOnce {
if (_coreVault == address(0)) {
revert("Not zero address");
}
coreVault = _coreVault;
setCoreVaultCalled = true;
emit SetCoreVaultAddress(msg.sender, _coreVault);
}BVSS
Recommendation
The coreVault address could be declared as immutable and set in the constructor. If the recommendation is applied, it would also be possible to remove the setCoreVaultAddress() function, the calledOnce modifier and the setCoreVaultCalled variable.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.15 Contract Name Reused in Different Files
//
Description
The name ReentrancyGuardProxy is used more than once to declare a library or contract inside the project. Specifically:
ReentrancyGuardProxyinsidecontracts/marketplace/CoreVault.solReentrancyGuardProxyinsidecontracts/marketplace/MergeMarketplaceStrategy.sol
BVSS
Recommendation
As indicated in the finding "Direct Inclusion and Modification of OpenZeppelin Modules Leading to Inconsistencies", consider using the well-known OpenZeppelin modules. If not, consider unifying all repeated contracts in a single file.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.16 Owner Can Renounce Ownership
//
Description
It was identified that the CoreVault and MergeMarketplaceStrategy contracts indirectly inherit from Ownable2Step through OnwnableWithPausable. In the Ownable2Step contract, the renounceOwnership() function is used to renounce the Owner permission. Renouncing ownership before transferring would result in the contract having no owner, eliminating the ability to call privileged functions.
/**
* @dev Leaves the contract without owner. It will not be possible to call
* `onlyOwner` functions. Can only be called by the current owner.
*
* NOTE: Renouncing ownership will leave the contract without an owner,
* thereby disabling any functionality that is only available to the owner.
*/
function renounceOwnership() public virtual onlyOwner {
_transferOwnership(address(0));
}Furthermore, the contract owner or single user with a role is not prevented from renouncing the role/ownership while the contract is paused, which would cause any user assets stored in the protocol, to be locked indefinitely.
BVSS
Recommendation
It is recommended that the Owner cannot call renounceOwnership() without first transferring ownership to another address. In addition, if a multi-signature wallet is used, the call to the renounceOwnership() function should be confirmed for two or more users.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.17 EnumerableSet.remove() in Loop Corrupts The Set Order
//
Description
The receivers global state variable in MergeMarketplaceStrategy is of type EnumerableSetUpgradeable. If the order of an EnumerableSet is required, removing items in a loop using at() and remove() corrupts this order. This finding has been reported as informational because the developer team indicated that order is not currently important, but it is important to have this in mind for future reference.
BVSS
Recommendation
Consider using a different data structure or removing items by collecting them during the loop, then removing after the loop.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.18 Incorrect bounds checking in getReceivers() reverts with empty receivers
//
Description
In MergeMarketplaceStrategy.sol, the getReceivers() function has a logical error in its bounds checking:
function getReceivers(uint256 start, uint256 end) public view returns (address[] memory) {
require(start < end && end <= receivers.length(), "Invalid range");
address[] memory result = new address[](end - start);
for (uint256 i = start; i < end; i++) {
result[i - start] = receivers.at(i);
}
return result;
}When
receivers.length() == 0, the function will always revert because:If
end > 0: reverts becauseend <= receivers.length()is falseIf
end == 0: reverts becausestart < endisfalseTherefore, no valid inputs exist when the list is empty
BVSS
Recommendation
Modify the bounds checking to handle empty lists correctly.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.19 Incomplete NatSpec Documentation
//
Description
The B14G project lacks comprehensive NatSpec comments for functions, state variables, and contracts. NatSpec is a widely adopted standard for documenting Solidity contracts, providing clear and structured explanations for developers, auditors, and end-users.
BVSS
Recommendation
Adopt and implement NatSpec comments across all contracts, functions, and state variables. Use the following structure as a guideline:
Contract-Level Documentation: Include a brief overview of the contract's purpose, scope, and high-level details. For example:
Function-Level Documentation: Document each function using NatSpec annotations, detailing:
@paramdescriptions for function parameters.@returndescriptions for return values.@devnotes for developers about implementation details or caveats.@noticefor user-facing descriptions.
State Variable Documentation: Document each variable with a concise explanation of its purpose and usage.
Global Guidelines:
Use tools like
solhintto enforce NatSpec standards.Regularly review documentation to ensure alignment with code updates.
By adding NatSpec documentation, the project can improve code clarity, facilitate audits, and enhance developer and user trust in the protocol.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.20 Potential License Incompatibilities
//
Description
The project contains contracts with varying SPDX license identifiers:
Some contracts specify
// SPDX-License-Identifier: Apache-2.0.Others specify
// SPDX-License-Identifier: MIT.Some use
// SPDX-License-Identifier: UNLICENSED.
This inconsistency can result in potential license incompatibilities or legal ambiguities regarding the use, distribution, and modification of the codebase. Specifically:
The MIT License is permissive, allowing free use, modification, and redistribution with attribution.
The Apache 2.0 License is also permissive but includes explicit patent grants and requires a more detailed notice, including a copy of the license and a notice of any modifications.
The UNLICENSED identifier indicates that the code is not licensed under any open-source terms, which may default to "all rights reserved" in some jurisdictions, limiting its usability.
While the MIT and Apache 2.0 licenses are generally compatible with each other, mixing them without clear documentation can create confusion. The presence of UNLICENSED files further complicates the legal standing of the codebase.
BVSS
Recommendation
To mitigate potential legal risks:
Standardize Licensing:
Choose a single open-source license that aligns with the project's goals and ensure all contracts uniformly declare this license.
If multiple licenses are necessary, clearly document which parts of the codebase are under which licenses and ensure they are compatible.
Avoid
UNLICENSEDIdentifier:Refrain from using the
UNLICENSEDidentifier unless the intention is to restrict usage. If the code is meant to be open-source, apply an appropriate open-source license.
Review License Compatibility:
If retaining multiple licenses, consult with legal counsel to ensure compatibility and compliance with all applicable licensing terms.
By standardizing the licensing across the codebase and ensuring clarity in licensing terms, the project can prevent legal ambiguities and facilitate easier use, distribution, and contribution.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.21 Lack of Event Emission
//
Description
It has been observed that some functionalities are missing event emissions. Events are essential for notifying external observers about critical state changes within a smart contract. They allow transaction initiators and external monitoring tools to track actions, enhancing transparency and usability.
Failing to emit events can lead to:
Reduced transparency of critical state changes.
Challenges for users and developers in debugging and auditing.
Missed opportunities for off-chain systems to react to state changes effectively.
Examples:
All
initialize()functions of the project are missing an event emissionupdateDualCore()andupdateMarketplace()inMergeMarketplaceStrategy.
This list is not exhaustive, and a thorough review of the entire codebase is recommended to identify additional instances where event emissions can improve transparency and traceability.
BVSS
Recommendation
All functions updating important parameters should emit events.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.22 Debugging Import Included in Production Code
//
Description
Most contracts in scope include the following import:
import "hardhat/console.sol";The console.sol library is a debugging utility from Foundry, typically used for logging during development and testing. Including it in production contracts increases gas costs and can unintentionally expose sensitive information or internal logic.
BVSS
Recommendation
Remove the hardhat/console.sol import and any associated debugging statements from production code before deployment.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.23 Magic Numbers in Use
//
Description
In programming, "magic numbers" refer to the use of hard-coded numerical or string values directly in the code without clear indication of their purpose or origin. The use of magic numbers can lead to confusion and make the codebase more difficult to understand, maintain, and update.
Several instances of magic numbers were found in the provided contracts. These values lack meaningful context, making it unclear whether they are arbitrary, derived from a specific standard, or require future modification. Their presence increases the likelihood of errors during maintenance or updates.
In
CoreVault.sol:
require(_fee < 10000, "Invalid fee");The maximum fee in CoreVault is 10_000, but 1_000 in Marketplace.
This list is not exhaustive, and it is recommended to review the entire codebase to identify additional instances where magic numbers are used.
BVSS
Recommendation
To improve code maintainability, readability, and reduce the risk of potential errors, it is recommended to replace magic numbers with well-defined constants. By using constants, developers can provide clear and descriptive names for specific values, making the code easier to understand and maintain. Additionally, updating the values becomes more straightforward, as changes can be made in a single location, reducing the risk of errors and inconsistencies. For large numbers, consider using scientific notation (e.g., 1e4).
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.24 Unlocked Pragma Compiler
//
Description
The files in scope currently use floating pragma version ^0.8.0, which means that the code can be compiled by any compiler version that is greater than or equal to 0.8.0, and less than 0.9.0. It is recommended that contracts should be deployed with the same compiler version and flags used during development and testing. Locking the pragma helps to ensure that contracts do not accidentally get deployed using another pragma. For example, an outdated pragma version might introduce bugs that affect the contract system negatively.
BVSS
Recommendation
Lock the pragma version to the same version used during development and testing.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.25 Use of Revert Strings Instead of Custom Error
//
Description
In Solidity smart contract development, replacing hard-coded revert message strings with the Error() syntax is an optimization strategy that can significantly reduce gas costs. Hard-coded strings, stored on the blockchain, increase the size and cost of deploying and executing contracts.
The Error() syntax allows for the definition of reusable, parameterized custom errors, leading to a more efficient use of storage and reduced gas consumption. This approach not only optimizes gas usage during deployment and interaction with the contract but also enhances code maintainability and readability by providing clearer, context-specific error information.
BVSS
Recommendation
It is recommended to replace hard-coded revert strings in require statements for custom errors, which can be done following the logic below.
1. Standard require statement (to be replaced):
require(condition, "Condition not met");2. Declare the error definition to state
error ConditionNotMet();3. Use the Custom Error in require or if statements.
Using custom errors inside require statements is only available from Solidity versions 0.8.26 and above. In case of older compiler version, consider using if statements + revert with Custom Error.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.26 Consider Using Named Mappings
//
Description
The project could be upgraded to a more recent Solidity version (greater than 0.8.18), which supports named mappings. Using named mappings can improve the readability and maintainability of the code by making the purpose of each mapping clearer. This practice helps developers and auditors understand the mappings' intent more easily.
BVSS
Recommendation
Consider refactoring the mappings to use named arguments, which will enhance code readability and make the purpose of each mapping more explicit.
For example, on MergeMarketplaceStrategy.sol, instead of declaring:
mapping(address => StakeInfo) public stakedOnReceivers;It could be declared as:
mapping(address receiver => StakeInfo stakeInfo) public stakedOnReceivers;Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.27 Style Guide Optimizations
//
Description
The project codebase contains several stylistic inconsistencies and deviations from Solidity best practices, which, while not directly impacting functionality, reduce code readability, maintainability, and adherence to standard conventions. Addressing these inconsistencies can enhance the clarity and professionalism of the code.
Whitespace issues: The first example below has two spaces between
publicanduserStake. The second example is missing a whitespace between(uint256)and{.
mapping(address => Stake) public userStake;
...
function getStakeOnCandidate(address user, address candidate) public view returns (uint256){Use of
publicWhereexternalCould Be Used: Certainpublicfunctions could be declared asexternalto potentially save gas and adhere to best practices.
Redundant Use of block.timestamp in Event Parameters: This use of
block.timestampas an event parameter is redundant because the timestamp of when the event is emitted is already included in the transaction metadata and can be accessed directly from the event logs. Including it as an explicit parameter increases the size of the emitted event, leading to slightly higher gas costs without adding meaningful value.
event Withdraw(uint indexed timestamp, uint amount, uint receiveAmount);
event ClaimReward(uint indexed timestamp, uint rewardAmount);Not Fully Leverage Named Returns: While some functions do use named returns, others do not.
Use of Whole File Imports Instead of Named Imports: Full file imports are used across the codebase, which may include unnecessary code and reduce clarity. Example from
MergeMarketplaceStrategy.sol:
import "../interfaces/IStrategy.sol";
import "../utils/OnwnableWithPausable.sol";
import "../library/Address.sol";
import "../interfaces/IMarketplace.sol";
import "../interfaces/IRewardReceiver.sol";BVSS
Recommendation
Consider implementing style improvements highlighted above to improve the readability and consistency of the project.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.28 Cache Array Length Outside of Loop
//
Description
When the length of an array is not cached outside of a loop, the Solidity compiler reads the length of the array during each iteration. For storage arrays, this results in an extra sload operation (100 additional gas for each iteration except the first). For memory arrays, this results in an extra mload operation (3 additional gas for each iteration except the first).
Detecting loops that use the length member of a storage array in their loop condition without modifying it can reveal opportunities for optimization. See the following example in CoreVault.sol:
function withdraw() external payable whenNotPaused nonReentrant {
UnbondRecord[] storage records = unbondRecords[msg.sender];
if (records.length == 0) revert("Empty record");
uint totalAmount;
for (uint256 i = records.length; i != 0; i--) {
...BVSS
Recommendation
Cache the length of the (storage and memory) arrays in a local variable outside the loop to optimize gas usage. This reduces the number of read operations required during each iteration of the loop. See the example fixes below:
function withdraw() external payable whenNotPaused nonReentrant {
UnbondRecord[] storage records = unbondRecords[msg.sender];
uint256 _recordsLength = records.length;
if (_recordsLength == 0) revert("Empty record");
uint totalAmount;
for (uint256 i = _recordsLength; i != 0; i--) {
...Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.29 Events Missing Indexed Fields
//
Description
Indexed event fields make the data more quickly accessible to off-chain tools that parse events, and add them to a special data structure known as "topics" instead of the data part of the log. A topic can only hold a single word (32 bytes) so if you use a reference type for an indexed argument, the Keccak-256 hash of the value is stored as a topic instead.
Each event can use up to three indexed fields. If there are fewer than three fields, all the fields can be indexed. It is important to note that each index field costs extra gas during emission, so it's not necessarily best to index the maximum allowed fields per event (three indexed fields).
This is specially recommended when gas usage is not particularly of concern for the emission of the events in question, and the benefits of querying those fields in an easier and straight-forward manner surpasses the downsides of gas usage increase.
BVSS
Recommendation
Consider adding the indexed keyword when declaring events, considering the following example in Marketplace.sol:
event Paused(address indexed account);
event Unpaused(address indexed account);Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.30 Mixed msg.sender and _msgSender
//
Description
The contracts in scope use msg.sender in some places and _msgSender() in others, despite inheriting context logic from OpenZeppelin. Even though meta-transactions may not be utilized, this inconsistency can introduce confusion and potential issues if meta-transactions or proxies are adopted in the future. In particular, _msgSender() properly reflects the original sender in scenarios involving relayers or proxies, whereas msg.sender might not.
BVSS
Recommendation
To maintain consistency and avoid potential issues with mixed usage, it is recommended to use _msgSender() exclusively throughout the codebase. This ensures a uniform approach to retrieving the caller's address and provides better compatibility with meta-transactions or proxies where _msgSender() may be overridden to return a different value than msg.sender.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.31 Inconsistency Declaring uint256/uint
//
Description
During the security review, it was observed that the contract uses both uint and uint256 types inconsistently across functions, events, and variable declarations. Although uint is an alias for uint256 in Solidity, inconsistency in type usage can reduce code readability and may lead to confusion for developers maintaining the contract.
Examples:
In
CoreVault.sol:
function initialize(address _owner, address _operator, uint _withdrawFee, uint _rewardFee, uint256 _unlockPeriod, uint256 _maxCap) public { Notice _withdrawFee is uint and _unlockPeriod is of type uint256.
event Unbond(address indexed user, uint256 coreAmount, uint256 dualCoreAmount, uint unlockTime);Notice coreAmount and dualCoreAmount are uint256, but unlockTime is of type uint.
Such inconsistencies can make it difficult to maintain code clarity and may lead to unnecessary type casting or confusion during contract upgrades.
BVSS
Recommendation
For consistency across the contract, it is recommended to declare all integer variables using a single type. Since uint256 is the preferred standard in Solidity, you can refactor the code by changing the few instances of uint to uint256.
In
CoreVault.sol:
function initialize(address _owner, address _operator, uint256 _withdrawFee, uint256 _rewardFee, uint256 _unlockPeriod, uint256 _maxCap) public { Alternatively, if you prefer brevity and are not concerned about explicitness, you may change all uint256 types to uint consistently throughout the contract. This will improve maintainability and ensure clarity for future developers.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
7.32 Unused or Dead Code
//
Description
During the security assessment of the smart contracts, several instances of unused code were identified. These unnecessary components can clutter the codebase, reduce readability, and potentially lead to confusion during development or auditing. Additionally, unused imports may slightly increase the compiled contract's bytecode size, affecting deployment and execution costs.
An unused global state variable in
CoreVault.sol:
uint256 public minAmount;Unused
internalfunctions inCoreVault.sol:
function initialize_ReentrancyGuard() internal {
...
function _reentrancyGuardEntered() internal view returns (bool) {Unused
internalfunctions inMergeMarketplaceStrategy.sol:
function initialize_ReentrancyGuard() internal {
...
function _reentrancyGuardEntered() internal view returns (bool) {BVSS
Recommendation
For better clarity, consider removing all unused code.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.33 Legacy/Confusing Naming
//
Description
The project’s ERC20 token is named dualCore, yet the code uses the same identifier in two different contexts:
In CoreVault, the
dualCorevariable represents theERC20token.In MergeMarketplaceStrategy, the
dualCorevariable is used to refer to theCoreVaultcontract.
This dual usage of the term dualCore can cause confusion for developers and auditors, potentially leading to integration or upgrade errors due to unclear semantics.
BVSS
Recommendation
Standardize naming conventions to improve clarity. For example, consider renaming:
The
dualCorevariable in CoreVault todualCoreToken(or a similar descriptive name), andThe
dualCorevariable in MergeMarketplaceStrategy tocoreVaultor another name that clearly indicates its purpose.
Clear and distinct naming will reduce ambiguity, ease future audits, and prevent potential integration mistakes.
Remediation
PENDING: The B14G team indicated that they will be addressing this finding in the future.
7.34 Ignored Return Values
//
Description
In Solidity, return values often provide critical information about the success or failure of an operation. Disregarding these values can result in missed error handling.
The following instances were identified:
In
CoreVault.sol:
function stake() external payable whenNotPaused nonReentrant {0
claimReward();
...
...
function withdrawDirect(uint256 dualCoreAmount, bool claim) external payable whenNotPaused nonReentrant {
if (claim) claimReward();
...In
MergeMarketplaceStrategy.sol:
function claimReward() public returns (uint reward) {
...
IMarketplace(marketplace).claimCoreRewardProxy(claimParams);
...BVSS
Recommendation
It is recommended to:
Handle All Return Values: Review all instances of ignored return values and ensure they are either explicitly checked or deemed unnecessary with proper documentation.
Update Affected Functions: Refactor the relevant functions to utilize or log return values for additional validation and error handling.
By addressing this issue, the contract's robustness and reliability will be improved, ensuring that critical operations are validated and potential errors are caught effectively.
Remediation
ACKNOWLEDGED: The B14G team acknowledged this finding.
8. Automated Testing
Static Analysis Report
Description
Halborn used automated testing techniques to enhance the coverage of certain areas of the smart contracts in scope. Among the tools used was Slither, a Solidity static analysis framework. After Halborn verified the smart contracts in the repository and was able to compile them correctly into their abis and binary format, Slither was run against the contracts. This tool can statically verify mathematical relationships between Solidity variables to detect invalid or inconsistent usage of the contracts' APIs across the entire code-base.
All issues identified by Slither were proved to be false positives or have been added to the issue list in this report.
Output
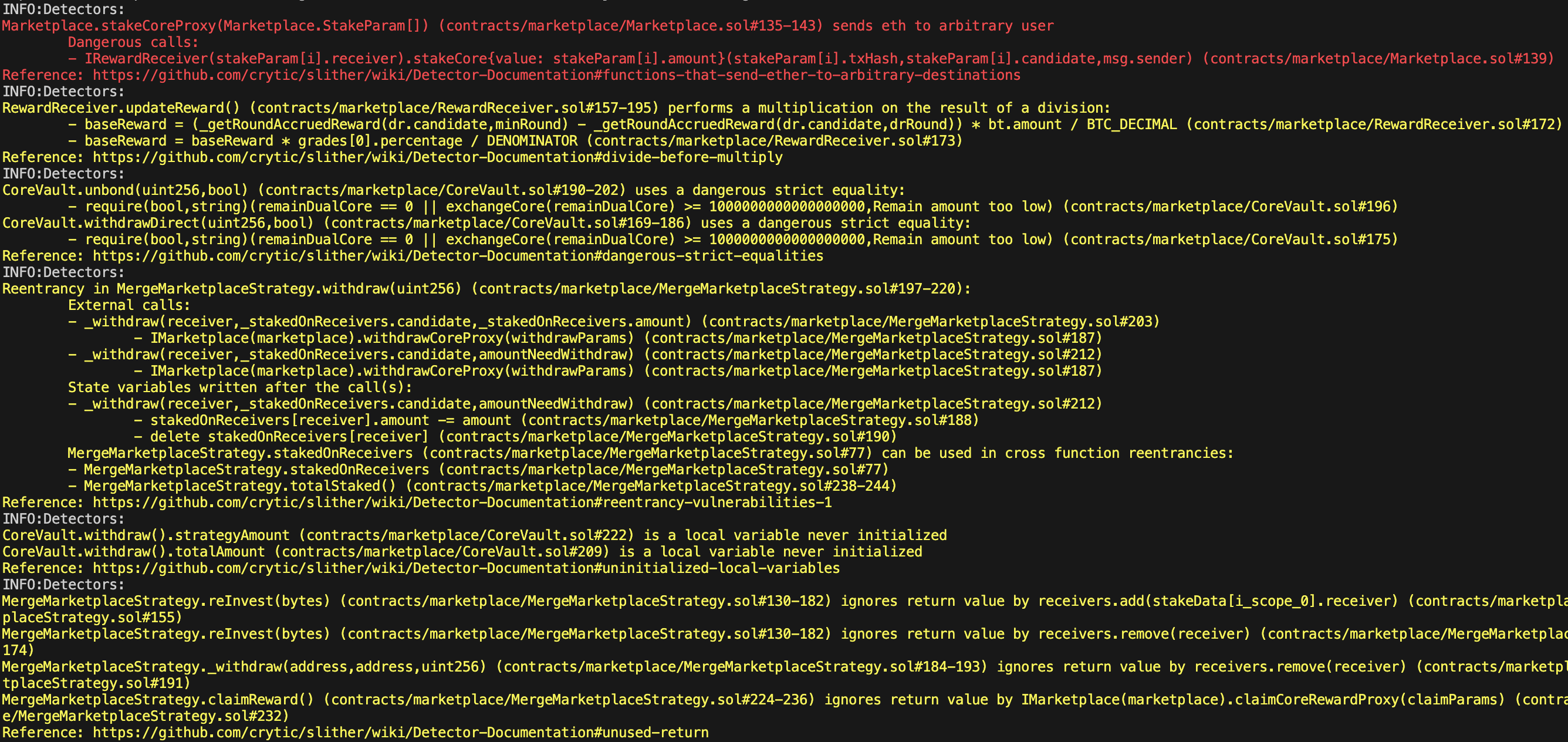
Halborn strongly recommends conducting a follow-up assessment of the project either within six months or immediately following any material changes to the codebase, whichever comes first. This approach is crucial for maintaining the project’s integrity and addressing potential vulnerabilities introduced by code modifications.
Table of Contents
- 1. Introduction
- 2. Assessment summary
- 3. Test approach and methodology
- 4. Risk methodology
- 5. Scope
- 6. Assessment summary & findings overview
- 7. Findings & Tech Details
- 7.1 Incorrect order of modifiers: nonreentrant should be the first
- 7.2 Non-payable owner would dos corevault
- 7.3 Initializers could be front-run
- 7.4 Implementation contracts can be initialized
- 7.5 Inconsistent timestamp comparisons exclude exact unlock time
- 7.6 Ineffective remaining dualcore balance check
- 7.7 Lack of storage gap in upgradeable contract
- 7.8 Division by zero not prevented
- 7.9 Missing input validation
- 7.10 Missing array length validation in reinvest
- 7.11 Potential rounding errors
- 7.12 Centralization risk
- 7.13 Direct inclusion and modification of openzeppelin modules leading to inconsistencies
- 7.14 Corevault in dualcore address could be immutable
- 7.15 Contract name reused in different files
- 7.16 Owner can renounce ownership
- 7.17 Enumerableset.remove() in loop corrupts the set order
- 7.18 Incorrect bounds checking in getreceivers() reverts with empty receivers
- 7.19 Incomplete natspec documentation
- 7.20 Potential license incompatibilities
- 7.21 Lack of event emission
- 7.22 Debugging import included in production code
- 7.23 Magic numbers in use
- 7.24 Unlocked pragma compiler
- 7.25 Use of revert strings instead of custom error
- 7.26 Consider using named mappings
- 7.27 Style guide optimizations
- 7.28 Cache array length outside of loop
- 7.29 Events missing indexed fields
- 7.30 Mixed msg.sender and _msgsender
- 7.31 Inconsistency declaring uint256/uint
- 7.32 Unused or dead code
- 7.33 Legacy/confusing naming
- 7.34 Ignored return values
- 8. Automated Testing
// Download the full report
* Use Google Chrome for best results
** Check "Background Graphics" in the print settings if needed
